ICF hosts our annual CyberSci Symposium at our headquarters conference center in Fairfax, VA. This premier science and technology event allows for U.S. Government, academia and industry professionals to discuss emerging RD challenges, cybersecurity trends, emerging technologies, best practices and strategies around the toughest issues facing cybersecurity. The past Symposium focused on urgent threats impacting the whole of nation, commercial and network infrastructures and the security of cloud networks and providers.
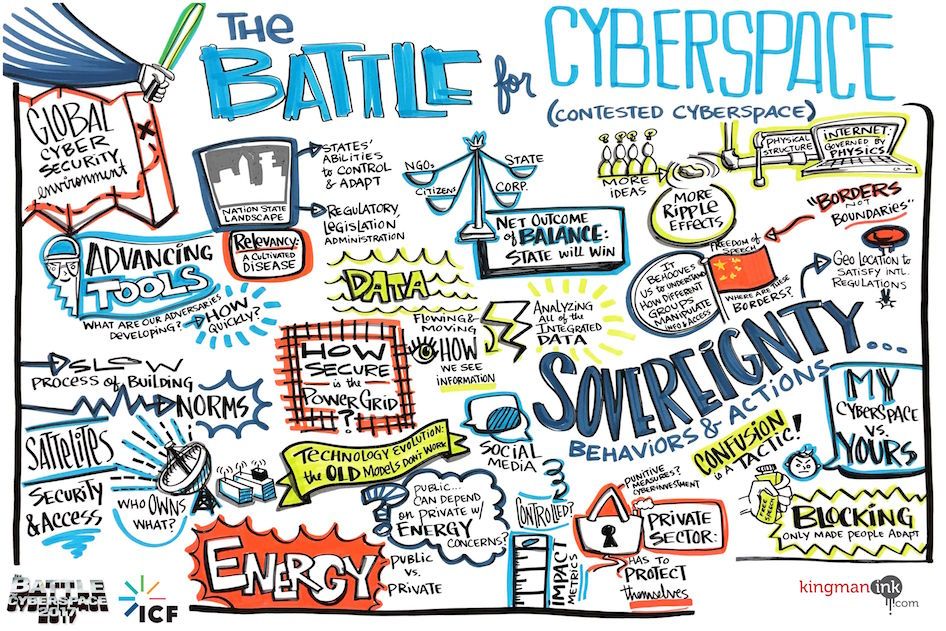
What Did We Learn at CyberSci 2018?
This year’s cybersecurity events have revealed a glaring similarity between the public and private sectors: our operations remain vulnerable to clear and present threats. We’ll continue to reveal lessons learned and actionable takeaways that you can plug into your organization—and avoid repeating history.